When evaluating firewall solutions on Azure, a key decision is whether to use the native Azure Firewall or opt for a third-party solution. Many Cloud Engineers hesitate to choose a third-party firewall, feeling they might miss out on native Azure features. However, at Codify, we recommend using the same edge networking solution in Azure as on-premises. This approach ensures a consistent, streamlined security strategy—without compromising on functionality.
In this article, we’ll show how Codify deploys FortiGates on Azure to overcome the limitations of Azure’s native firewall and detail how it delivers seamless integration with Azure so you can have your cake and eat it too.
Key Limitations of Azure Firewalls
For customers navigating a hybrid cloud environment, using the same edge firewall in Azure as on-premises offers clear advantages. However, the simplicity of Azure Firewall can be appealing—and potentially misleading. Deployment is as easy as checking a box in the Azure VNet setup, but this convenience can lead to oversights and, over time, the accumulation of technical debt, especially when it’s time to productionise your cloud environment.
A recurring issue with Azure Firewall is the lack of operational ownership from the IT Security team. Often deployed by infrastructure teams with minimal security oversight, it can lead to missed tasks like rule reviews and threat monitoring, leaving security gaps.
If these people and process challenges aren’t reason enough to reconsider Azure Firewall, let’s delve into some technical limitations.
- Limited IP Group Sharing: Azure Firewall’s IP groups are confined within Azure and lack cross-region flexibility. With a limit of only 200 IP groups, they can be exhausted quickly in even the simplest environment.
- Delayed Logging: Azure Firewall’s traffic logs in Log Analytics have a delay, typically between 2-5 minutes. This lag can make real-time monitoring and network troubleshooting difficult.
- Complex Data Queries: To extract and transform specific data, firewall admins need KQL (Kusto Query Language) grandmasters. Without advanced knowledge, making sense of log data can be a time-consuming challenge.
- Minimal Reporting Options: Built-in reports are sparse, with only a few templated KQL queries available, requiring more effort to generate useful insights.
- No VPN Termination Support: Azure Firewall doesn’t terminate P2S (Point-to-Site) or S2S (Site-to-Site) VPN connections, which is a common requirement for our customers.
- Costly Premium Features: Many customers need Azure Firewall’s Premium tier features to meet security requirements (IDPS, TLS inspection, URL filtering) but the costs add up quickly.
- Slow Policy Changes: Policy changes in Azure Firewall are not only slow to apply, but must also be made individually, limiting agility in dynamic environments.
As a whole, these limitations can make Azure Firewalls less practical for many organisations, especially those with complex hybrid environments.
Reasons to Choose FortiGates on Azure
At Codify, we’ve chosen to specialise in FortiGate firewalls because of Fortinet’s investment to build a truly integrated firewall solution with Azure reference architectures. For many of our customers already using FortiGate firewalls on-premises, extending this solution to the cloud has proven to be a seamless and effective choice.
Our partnership with Fortinet has allowed us to go beyond a simple Next-Next-Next deployment to create a templated solution that follows the reference architectures and enables the cloud integrations on offer to deliver an integrated Azure solution design from the get-go.
Here, we’ll explore the three keyways we’ve bridged the gap to deliver a solution that aligns with the needs of hybrid cloud environments while enhancing security and operational ease.
Network Design
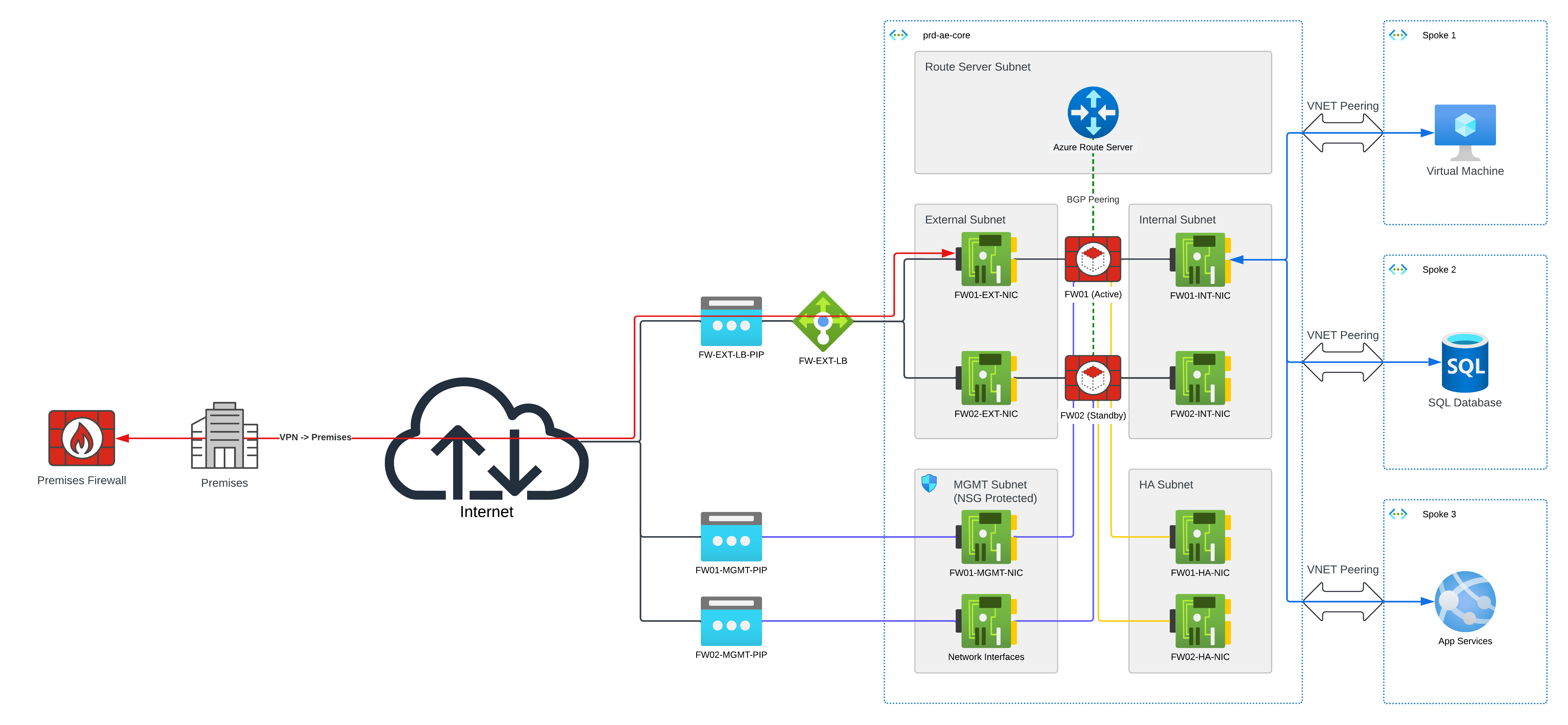
Codify recommends avoiding Internal Load Balancers and static routing with Route Tables for FortiGate deployments on Azure, as these approaches compromise OSI layer independence and network flexibility. Instead, we advocate for dynamic routing through Azure Route Server with BGP, ensuring resilient, Layer 3–focused routing and supporting secure, adaptable networks.
These recommendations aren’t just theoretical. They’re lessons learned from years of experience building and managing Azure-based firewalls. This strategy mitigates operational and security challenges while enabling future scalability, allowing customers to leverage advanced FortiGate features, such as VDOMs and Policy Zones, as their hybrid cloud environments evolve.
Detailed Design Rationale
Creating a resilient and effective network design is key when deploying FortiGate solutions in Azure. At Codify, we’ve found that certain design principles enhance both reliability and security, while others can introduce unnecessary complexity or limitations. Here, we outline the key network design recommendations we follow to ensure the best performance and scalability for our customers
Avoid Internal Load Balancers for FortiGate Deployments on Azure
We advise against using Azure Internal Load Balancers (ILBs) for FortiGates on Azure. This recommendation is rooted in a fundamental network design principle: each layer of the OSI model should function independently. In practice, this means that functions at one layer shouldn’t overly depend on another, as it creates interdependencies that can lead to operational issues.
When it comes to Azure FortiGates and ILBs:
- Intended Use Case: Azure’s ILBs are designed to load balance next-hop routing (Layer 3) by monitoring health using TCP checks (Layer 4) within backend pools. This setup aims to provide either active-passive or n-active load balancing.
- Design Issue: Relying on TCP checks for a Layer 3 routing function violates the layer independence principle. Faults at the transport layer (such as TCP session issues) can fail to accurately reflect the health and functionality of the IP routing layer, resulting in potential instability and reliability issues.
- Recommendation: Rather than relying on ILBs, we recommend using dynamic routing with BGP (Border Gateway Protocol) via Azure Route Server. This approach strengthens Layer 3 resilience, enabling the network layer to operate independently and reducing potential transport-layer conflicts.
Minimise Static Routing for FortiGates on Azure
Codify also recommends against static routing with Route Tables when configuring FortiGates on Azure. This advice aligns with the principle of dynamic routing, which supports automatic adjustments to routing paths in response to network changes.
- Azure Route Tables: By relying on static routing rules, Route Tables override Azure’s default dynamic routing, explicitly controlling traffic flow across Azure virtual networks. While static routing can provide more direct control, it lacks the flexibility of dynamic adjustments.
- Design Limitation: Using static routes makes subnets vulnerable, as they’re not secured by default. This can create potential exposure points, especially in environments with complex and evolving network architectures.
- Recommendation: To maintain secure and adaptable routing, we recommend using Azure Route Server to establish a BGP connection between FortiGates and Azure’s software-defined network (SDN). Dynamic routing enables load balancing, better resiliency, and an agile response to network changes, which significantly reduces the need for manual intervention and minimises downtime.
FortiGate Limitations with Internal Load Balancers
When deploying FortiGate firewalls in Azure, there are additional factors to consider, particularly concerning Internal Load Balancers:
- Internal Load Balancer Constraints: Network flow symmetry limitations in Azure ILBs restrict the deployment of additional network interfaces. This limitation impacts customers’ ability to use advanced FortiGate features, such as Virtual Domains (VDOMs) and Policy Zones, which require multiple NICs and offer flexible traffic segmentation and security policy management.
We suggest leveraging dynamic routing to support resilience and scalability in FortiGate deployments on Azure. This approach not only enhances reliability but also enables future growth by allowing the integration of additional interfaces to different Zones or VDOMs. By doing so, customers gain a more versatile firewall setup, capable of adapting to the evolving demands of hybrid cloud environments.
Operational Management of FortiGates on Azure
Effective operational management is crucial to maximising the value of a FortiGate deployment on Azure. Codify has developed several best practices to streamline both administrative access and security monitoring, leveraging Azure’s ecosystem for seamless integration.
Entra ID SSO for Secure, Centralised Access
We recommend using Entra ID (formerly Azure Active Directory) Single Sign-On (SSO) for FortiGate administration. By integrating Entra ID, administrators gain secure, centralised access without the need for separate FortiGate credentials, reducing password fatigue and enhancing security. Additionally, remote users benefit from FortiClient VPN’s SSO capability, which allows them to authenticate using their Entra ID credentials. This setup offers a consistent, streamlined experience for both admins and end users, enhancing productivity while maintaining high security standards.
SSH Key Pairs for Local Accounts
For local accounts on the FortiGate, we suggest leveraging SSH key pairs stored in Azure. This approach eliminates the need for password-based login for local access, further reducing the risk of unauthorised access. By using Azure’s native SSH key management capabilities, administrators can maintain secure, efficient access without managing additional passwords.
Enhanced Security Monitoring with Azure Sentinel
To ensure comprehensive visibility across the network, we recommend forwarding FortiGate logs to Azure Sentinel. By doing so, you can leverage Sentinel’s advanced data collection, analytics, and incident management capabilities. This setup allows you to use Sentinel as a central SIEM solution, gaining insights into security events, identifying potential threats, and responding quickly to incidents. With FortiGate logs integrated into Sentinel, customers can monitor and analyse their FortiGate data alongside other sources within Azure, creating a robust, unified view of their security posture.
Optimising FortiGate Deployments on Azure
After deploying FortiGate on Azure, there are several key ways to optimise both cost and performance, especially as the environment transitions into production. As FortiGates on Azure are deployed as VMs, customers have multiple options for cost optimisation, which we recommend adding to your post-go-live or hyper-care checklist.
Cost-Effective Licensing Options
FortiGate licensing on Azure can be handled in two ways: either through the Azure Marketplace or by using a Bring Your Own License (BYOL) key. While both options offer flexibility, it’s important to note that you can’t switch between them without redeploying the FortiGate VM. Fortunately, redeployment is a straightforward process when using Azure ARM templates for the base infrastructure, and you can easily reuse an exported configuration to get back up and running quickly.
Leveraging VM Reservations for Savings
One of the most effective ways to reduce ongoing costs is by reserving capacity for the FortiGate VMs, as these resources typically run 24/7. We recommend using the F-series SKU, which offers a higher NIC-to-CPU ratio, optimising network throughput and processing efficiency. A 3-year reservation on this SKU can yield savings of up to 57%, making it a valuable option for long-term deployments.
With these optimisation strategies, customers can ensure their FortiGate deployment on Azure remains both cost-effective and high-performing as they scale.
Conclusion
You shouldn’t feel like you are compromising by choosing a third-party option over the Azure native firewall. In fact, choosing the right firewall solution on Azure is critical for building a resilient, secure, and cost-effective cloud environment.
Codify’s extensive experience with FortiGate deployments on Azure has led us to develop best practices for network design, operational management, and cost optimisation, ensuring that customers can fully leverage the capabilities of FortiGate in the cloud.
By adhering to a dynamic routing approach, integrating with Entra ID SSO, and utilising Azure Sentinel for enhanced monitoring, we provide customers with a robust, scalable firewall setup that meets both current and future security needs.
Whether you’re new to FortiGate or looking to migrate from Azure Firewall, Codify is here to support you in building a secure and optimised cloud infrastructure – get in touch!
For more FortiGate tips and best practices, check out…
Deploying FortiGate’s on Azure with ExpressRoute & Azure Route Server – Codify
FortiGate Firewall as a Service for Azure
Codify FortiGate’s Bundle: Comprehensive, secure, and scalable next-generation firewall solutions for your Azure Cloud.
FortiGate Firewall as a Service for Azure | Codify Cloud Security AU